#cloud security and disaster recovery
Explore tagged Tumblr posts
Text
Dominating the Market with Cloud Power

Explore how leveraging cloud technology can help businesses dominate the market. Learn how cloud power boosts scalability, reduces costs, enhances innovation, and provides a competitive edge in today's digital landscape. Visit now to read more: Dominating the Market with Cloud Power
#ai-driven cloud platforms#azure cloud platform#business agility with cloud#business innovation with cloud#capital one cloud transformation#cloud adoption in media and entertainment#cloud computing and iot#cloud computing for business growth#cloud computing for financial institutions#cloud computing for start-ups#cloud computing for travel industry#cloud computing in healthcare#cloud computing landscape#Cloud Computing solutions#cloud for operational excellence#cloud infrastructure as a service (iaas)#cloud migration benefits#cloud scalability for enterprises#cloud security and disaster recovery#cloud solutions for competitive advantage#cloud solutions for modern businesses#Cloud storage solutions#cloud technology trends#cloud transformation#cloud-based content management#cloud-based machine learning#cost-efficient cloud services#customer experience enhancement with cloud#data analytics with cloud#digital transformation with cloud
1 note
·
View note
Text
https://www.bloglovin.com/@vastedge/hybrid-cloud-backup-strategy-specifics-benefits
Learn how to create a resilient hybrid cloud backup strategy that combines the best of both private and public clouds. Explore key considerations such as data security, cost management, and disaster recovery to ensure your data is protected and accessible at all times.
#hybrid cloud#cloud backup strategy#data backup#cloud security#disaster recovery#hybrid cloud benefits#cloud storage solutions.
0 notes
Text
(2024-05-01) Delivering A Demo About Reconnecting AD Back With Entra ID At "Troopers 2024"
Very proud (again!) to have been selected again to present at Troopers 2024! Somewhere in the week of June 24th – 28th, I will be challenging the demo gods for a full hour. Let’s just hope everything goes as planned! Last year at Troopers I presented about the “Best Practices for Resynchronizing AD and Entra ID After Forest Recovery”. This year, I will actually show you how this can be done for…
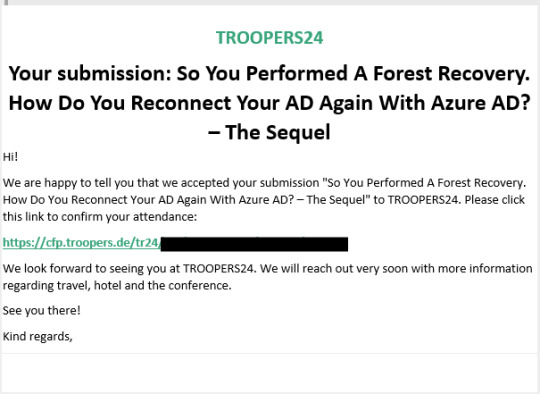
View On WordPress
#Active Directory#cybersecurity#Disaster Recovery#Entra Cloud Sync#Entra Connect Sync#Fixing Identity Data#GAP Analysis#PowerShell#Ransomware#Security#Tooling/Scripting
0 notes
Text
Secure out-of-band console and power management for Check Point security gateways - CyberTalk
New Post has been published on https://thedigitalinsider.com/secure-out-of-band-console-and-power-management-for-check-point-security-gateways-cybertalk/
Secure out-of-band console and power management for Check Point security gateways - CyberTalk
Contributed by WTI as part of Check Point’s CPX silver-level partner sponsorship opportunity. WTI is an industry leader in out-of-band network management.
Nobody has time to drive to a site when an ISP drops service or you simply need to reconfigure and/or reboot a switch, router or firewall. Your time is too valuable not to have an out-of-band solution in place. WTI out-of-band solutions comes with a cellular connect and fallback option that gives you secure remote access to console ports as well as control of individual power outlets when your network services are disrupted.
WTI out-of-band management solutions
WTI engineers and manufactures secure out-of-band management solutions for local and globally deployed networks. WTI out-of-band products are designed to ensure uninterrupted access to network devices and services by providing solutions to quickly and effectively respond to problems at distant or hard to reach equipment sites. When a router, switch or security appliance becomes inaccessible and interrupts network services, WTI out-of-band solutions provide redundant, remote console port management and power switching/reboot control to regain access and restore services in mission critical applications.
Even when the network is down, WTI out-of-band console server solutions can provide secure connectivity over primary and secondary ethernet and cellular LTE connections, allowing remote access to console ports and power control functions.
In addition, WTI DevOps allows administrators to configure, deploy and orchestrate WTI out-of-band management solutions across your entire network for automated provisioning, monitoring and disaster recovery of critical infrastructure. Features such as RESTful API, Ansible Playbooks and Python Scripting are supported.
Check Point Software Technologies and WTI
WTI offers a comprehensive out-of-band management strategy for Check Point Security Gateways, allowing your NOC to deal with equipment outages and resulting interruptions of network communication without the need to dispatch support teams to remote branch offices and data centers.
During network outages, WTI’s console server products allow you to establish remote out-of-band connections to console ports on security gateways via secure, authenticated communication protocols. If a reboot is needed, WTI Switched PDU products can provide remote out-of-band access to power switching functions at distant equipment sites. WTI also offers a combination console server plus switched PDU unit for applications that require both out-of-band console access and power reboot control.
WTI out-of-band centralized management provides access and control for all of your network devices, allowing for console data from multiple Check Point devices spread over a global network to be monitored, logged and available to administrators, simplifying the challenge of managing a large number of remote devices while minimizing resources.
With multiple connectivity options, WTI console servers including 4G LTE and/or dual Gigabit Ethernet ports can provide secure access to advanced DNS functions when primary and/or secondary ISP connections are switched or disconnected. WTI’s dual ethernet console servers allow you to remotely configure primary and secondary DNS settings and set up IP tables to maximize availability of security gateways during network outages, ensuring seamless transfers between primary and secondary ISPs. The optional 4G LTE internal modem provides a secure additional alternate path for out-of-band connectivity using security protocols such as IPSec and OpenVPN.
About WTI
WTI designs and manufactures Secure Out-of-Band Management Solutions for local and globally deployed networks. WTI provides redundant OOB console access and power control to mission critical infrastructure … even when the network is down. WTI products can be purchased factory direct and through various channel partners worldwide. Since 1964, WTI has maintained local in-house manufacturing, engineering and technical support. Learn more at www.wti.com.
About Check Point Software Technologies, Ltd.
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading AI-powered, cloud-delivered cyber security platform provider protecting over 100,000 organizations worldwide. Check Point leverages the power of AI everywhere to enhance cyber security efficiency and accuracy through its Infinity Platform, with industry-leading catch rates enabling proactive threat anticipation and smarter, faster response times. The comprehensive platform includes cloud-delivered technologies consisting of Check Point Harmony to secure the workspace, Check Point CloudGuard to secure the cloud, Check Point Quantum to secure the network, and Check Point Infinity Core Services for collaborative security operations and services.
WTI out-of-band management solutions provide Check Point security gateways with:
In-band and out-of-band console access from anywhere.
Remotely reconfigure, revive and restore gateways via SSH.
Connect via ethernet or cellular 4G LTE with optional failover.
Power cycle and monitoring capabilities.
Faster network issue resolution.
Application example
Challenge: Provide secure, authenticated access to configuration parameters on console ports on Check Point security gateways during outages.
Answer: WTI console servers with dual gig ethernet ports ensure secure console port connections via primary and secondary ethernet as well as OOB access via optional LTE cellular modem.
Results: If the primary in-band network fails, admins can initiate secure SSH connections to security gateway console ports via out-of-band, allowing access to configuration parameters and other data used to troubleshoot unresponsive devices and revive network services.
In conclusion, WTI out-of-band management solutions empower your team to regain control quickly and reduce network disruptions. Are you ready to save time, energy and resources? Let’s discuss how WTI can help!
#000#4g#ai#AI-powered#ansible#API#applications#challenge#channel#Channel partners#Check Point#Check Point Software#Cloud#cloud-delivered#CloudGuard#collaborative#communication#comprehensive#connectivity#CPX#critical infrastructure#cyber#cyber security#data#Data Centers#deal#devices#Devops#disaster recovery#DNS
0 notes
Text
Disaster Recovery Solutions: Safeguarding Business Continuity in an Uncertain World

In an era marked by unprecedented digital reliance, disaster recovery solution have risen to prominence as an essential safeguard for business continuity. This article delves into the critical realm of disaster recovery solutions, exploring their significance, the technology that underpins them, and the profound benefits they offer in ensuring uninterrupted operations, even in the face of adversity.
Understanding Disaster Recovery Solutions
Disaster recovery solutions are comprehensive strategies and technologies designed to protect an organization's critical data, applications, and IT infrastructure from disruptions caused by various calamities. These disruptions can encompass natural disasters like hurricanes and earthquakes, technological failures, cyberattacks, or even human errors. The primary goal of disaster recovery solutions is to enable a swift and seamless restoration of essential business functions, reducing downtime and its associated costs.
Why Disaster Recovery Solutions Matter
Mitigating Downtime: Downtime can be crippling, leading to lost revenue, productivity, and customer trust. Disaster recovery solutions aim to minimize downtime by swiftly restoring systems and data.
Preserving Data Integrity: In the digital age, data is the lifeblood of organizations. Disaster recovery solutions ensure the integrity of critical data, preventing loss or corruption.
Maintaining Business Reputation: Being able to continue operations in the wake of a disaster or disruption demonstrates resilience and commitment to clients and stakeholders, enhancing an organization's reputation.
Meeting Compliance Requirements: Many industries and regulatory bodies mandate the implementation of disaster recovery plans to protect sensitive data and maintain business continuity.
Key Elements of Disaster Recovery Solutions
Data Backup and Replication: Regular and automated backups of critical data, coupled with real-time data replication, ensure data availability even in the event of hardware failures or data corruption.
Redundant Infrastructure: Utilizing redundant servers, storage, and network infrastructure reduces the risk of single points of failure.
Disaster Recovery Testing: Regular testing and simulation of disaster scenarios help identify vulnerabilities and refine recovery processes.
Remote Data Centers: Storing data and applications in geographically distant data centers provides additional protection against localized disasters.
Cloud-Based Solutions: Cloud platforms offer scalable and cost-effective disaster recovery solutions, enabling quick recovery from virtually anywhere.
Benefits of Disaster Recovery Solutions
Minimized Downtime: Swift recovery ensures minimal disruption to business operations, reducing financial losses.
Data Resilience: Protection against data loss preserves critical information and intellectual property.
Improved Security: Disaster recovery solutions often include robust security measures, safeguarding against cyberattacks.
Regulatory Compliance: Meeting compliance requirements helps avoid potential legal and financial penalties.
Business Continuity: Demonstrating resilience reassures customers, partners, and employees, maintaining trust and business relationships.
Conclusion
In an unpredictable world where business continuity is non-negotiable, disaster recovery solutions provide the safety net organizations need to weather disruptions and emerge stronger. By embracing these solutions, businesses can not only protect their vital assets but also demonstrate unwavering commitment to their stakeholders. In an age of digital transformation, disaster recovery solutions are the linchpin of resilience, ensuring that, no matter what comes their way, businesses can keep moving forward.
#Secure Cloud Hosting#Data Center Services#Cloud Migration#cloud network security#internet solutions#disaster recovery solution#Managed cloud services#Cloud migration services
1 note
·
View note
Text
Exciting Mock interview with DevOps/AWS engineer #devops #cloud #aws #devopsengineer #cloudengineer
Interviewer: Welcome to this exciting mock interview for the role of a DevOps/AWS Engineer! Today, we have an enthusiastic candidate eager to showcase their skills. Let’s begin! Candidate: Thank you! I’m thrilled to be here. Interviewer: Great to have you. Let’s start with a classic question: What attracted you to the field of DevOps and working with AWS? Candidate: DevOps combines my passion…

View On WordPress
#Automation#AWS#CI/CD#cloud engineering#cloud technology#collaboration#communication#continuous integration#cost optimization#cross-functional teams#DevOps#disaster recovery#high availability#IaC#incident management#infrastructure as code#mock interview#performance optimization#scalability#security#tech trends
0 notes
Text
If you always found it challenging to manage your business’s IT needs? Get in touch with Clarity Technology Solutions. We investigate to find out what your company requires to succeed. We assure you that you will benefit greatly if you partner with us. Since 2005, companies have been reaching out to us.
#Data Recovery Delaware#Backup And Disaster Recovery Services#Managed IT Security Services Providers#Cybersecurity Ohio#Cyber Security Managed Service Providers#Managed Cloud Services Ohio#Professional Cloud Computing Services
0 notes
Text
Know About Cloud Computing Services - SecureTech

Introduction
In today's digital age, cloud computing has become an integral part of the business world. Companies are increasingly turning towards cloud computing services to enhance their operations and increase productivity. San Antonio, with its burgeoning technology sector, has become a hub for cloud computing services. One such company, SecureTech, is offering top-notch cloud computing services in San Antonio. In this article, we will explore the benefits of cloud computing and why SecureTech is the go-to company for businesses in San Antonio.
What is Cloud Computing?
Before delving into the benefits of cloud computing, it is essential to understand what it is. Cloud computing refers to the practice of using a network of remote servers hosted on the internet to store, manage, and process data. In simpler terms, it means using the internet to access software and applications that are not installed on your computer or device.
Benefits of Cloud Computing
There are numerous benefits of using cloud computing services, some of which are:
1. Cost-Effective
One of the primary benefits of cloud computing is its cost-effectiveness. It eliminates the need to invest in expensive hardware and software as everything is hosted on the cloud provider's servers.
2. Scalability
Cloud computing offers unparalleled scalability as businesses can easily scale up or down their operations depending on their requirements. This makes it an ideal solution for businesses with fluctuating workloads.
3. Accessibility
Cloud computing services allow businesses to access their data and applications from anywhere with an internet connection. This means that employees can work from anywhere, which enhances productivity and flexibility.
4. Security
Cloud computing services offer robust security measures to protect data and applications from unauthorized access, theft, or loss. Providers like SecureTech offer top-notch security measures to ensure that their clients' data is always secure.
Visit - https://www.getsecuretech.com/cloud-technologies/
#Cloud migration#Cloud storage#Cloud security#Virtualization#Private cloud#Hybrid cloud#Public cloud#Cloud backup#Disaster recovery#Cloud computing#Multi-cloud#Cloud-based#monitoring#Cloud deployment#Cloud scalability#Cloud performance
0 notes
Text
Here's the complete list of DHS flagged search terms. Don't use any of these on social media to avoid having the 3-letter agencies express interest in your activities!
DHS & Other Agencies
Department of Homeland Security (DHS)
Federal Emergency Management Agency (FEMA)
Coast Guard (USCG)
Customs and Border Protection (CBP)
Border Patrol
Secret Service (USSS)
National Operations Center (NOC)
Homeland Defense
Immigration Customs Enforcement (ICE)
Agent
Task Force
Central Intelligence Agency (CIA)
Fusion Center
Drug Enforcement Agency (DEA)
Secure Border Initiative (SBI)
Federal Bureau of Investigation (FBI)
Alcohol Tobacco and Firearms (ATF)
U.S. Citizenship and Immigration Services (CIS)
Federal Air Marshal Service (FAMS)
Transportation Security Administration (TSA)
Air Marshal
Federal Aviation Administration (FAA)
National Guard
Red Cross
United Nations (UN)
Domestic Security
Assassination
Attack
Domestic security
Drill
Exercise
Cops
Law enforcement
Authorities
Disaster assistance
Disaster management
DNDO (Domestic Nuclear Detection Office)
National preparedness
Mitigation
Prevention
Response
Recovery
Dirty Bomb
Domestic nuclear detection
Emergency management
Emergency response
First responder
Homeland security
Maritime domain awareness (MDA)
National preparedness initiative
Militia
Shooting
Shots fired
Evacuation
Deaths
Hostage
Explosion (explosive)
Police
Disaster medical assistance team (DMAT)
Organized crime
Gangs
National security
State of emergency
Security
Breach
Threat
Standoff
SWAT
Screening
Lockdown
Bomb (squad or threat)
Crash
Looting
Riot
Emergency Landing
Pipe bomb
Incident
Facility
HAZMAT & Nuclear
Hazmat
Nuclear
Chemical Spill
Suspicious package/device
Toxic
National laboratory
Nuclear facility
Nuclear threat
Cloud
Plume
Radiation
Radioactive
Leak
Biological infection (or event)
Chemical
Chemical burn
Biological
Epidemic
Hazardous
Hazardous material incident
Industrial spill
Infection
Powder (white)
Gas
Spillover
Anthrax
Blister agent
Exposure
Burn
Nerve agent
Ricin
Sarin
North Korea
Health Concern + H1N1
Outbreak
Contamination
Exposure
Virus
Evacuation
Bacteria
Recall
Ebola
Food Poisoning
Foot and Mouth (FMD)
H5N1
Avian
Flu
Salmonella
Small Pox
Plague
Human to human
Human to ANIMAL
Influenza
Center for Disease Control (CDC)
Drug Administration (FDA)
Public Health
Toxic
Agro Terror
Tuberculosis (TB)
Agriculture
Listeria
Symptoms
Mutation
Resistant
Antiviral
Wave
Pandemic
Infection
Water/air borne
Sick
Swine
Pork
Strain
Quarantine
H1N1
Vaccine
Tamiflu
Norvo Virus
Epidemic
World Health Organization (WHO and components)
Viral Hemorrhagic Fever
E. Coli
Infrastructure Security
Infrastructure security
Airport
CIKR (Critical Infrastructure & Key Resources)
AMTRAK
Collapse
Computer infrastructure
Communications infrastructure
Telecommunications
Critical infrastructure
National infrastructure
Metro
WMATA
Airplane (and derivatives)
Chemical fire
Subway
BART
MARTA
Port Authority
NBIC (National Biosurveillance Integration Center)
Transportation security
Grid
Power
Smart
Body scanner
Electric
Failure or outage
Black out
Brown out
Port
Dock
Bridge
Canceled
Delays
Service disruption
Power lines
Southwest Border Violence
Drug cartel
Violence
Gang
Drug
Narcotics
Cocaine
Marijuana
Heroin
Border
Mexico
Cartel
Southwest
Juarez
Sinaloa
Tijuana
Torreon
Yuma
Tucson
Decapitated
U.S. Consulate
Consular
El Paso
Fort Hancock
San Diego
Ciudad Juarez
Nogales
Sonora
Colombia
Mara salvatrucha
MS13 or MS-13
Drug war
Mexican army
Methamphetamine
Cartel de Golfo
Gulf Cartel
La Familia
Reynose
Nuevo Leon
Narcos
Narco banners (Spanish equivalents)
Los Zetas
Shootout
Execution
Gunfight
Trafficking
Kidnap
Calderon
Reyosa
Bust
Tamaulipas
Meth Lab
Drug trade
Illegal immigrants
Smuggling (smugglers)
Matamoros
Michoacana
Guzman
Arellano-Felix
Beltran-Leyva
Barrio Azteca
Artistics Assassins
Mexicles
New Federation
Terrorism
Terrorism
Al Queda (all spellings)
Terror
Attack
Iraq
Afghanistan
Iran
Pakistan
Agro
Environmental terrorist
Eco terrorism
Conventional weapon
Target
Weapons grade
Dirty bomb
Enriched
Nuclear
Chemical weapon
Biological weapon
Ammonium nitrate
Improvised explosive device
IED (Improvised Explosive Device)
Abu Sayyaf
Hamas
FARC (Armed Revolutionary Forces Colombia)
IRA (Irish Republican Army)
ETA (Euskadi ta Askatasuna)
Basque Separatists
Hezbollah
Tamil Tiger
PLF (Palestine Liberation Front)
PLO (Palestine Libration Organization)
Car bomb
Jihad
Taliban
Weapons cache
Suicide bomber
Suicide attack
Suspicious substance
AQAP (Al Qaeda Arabian Peninsula)
AQIM (Al Qaeda in the Islamic Maghreb)
TTP (Tehrik-i-Taliban Pakistan)
Yemen
Pirates
Extremism
Somalia
Nigeria
Radicals
Al-Shabaab
Home grown
Plot
Nationalist
Recruitment
Fundamentalism
Islamist
Weather/Disaster/Emergency
Emergency
Hurricane
Tornado
Twister
Tsunami
Earthquake
Tremor
Flood
Storm
Crest
Temblor
Extreme weather
Forest fire
Brush fire
Ice
Stranded/Stuck
Help
Hail
Wildfire
Tsunami Warning Center
Magnitude
Avalanche
Typhoon
Shelter-in-place
Disaster
Snow
Blizzard
Sleet
Mud slide or Mudslide
Erosion
Power outage
Brown out
Warning
Watch
Lightening
Aid
Relief
Closure
Interstate
Burst
Emergency Broadcast System
Cyber Security
Cyber security
Botnet
DDOS (dedicated denial of service)
Denial of service
Malware
Virus
Trojan
Keylogger
Cyber Command
2600
Spammer
Phishing
Rootkit
Phreaking
Cain and abel
Brute forcing
Mysql injection
Cyber attack
Cyber terror
Hacker
China
Conficker
Worm
Scammers
Social media
SOCIAL MEDIA?!
21 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Secure and Scalable Cloud Server Management at Atcuality
For businesses seeking to enhance scalability and maintain top-tier security, Atcuality provides unparalleled cloud server management services. Our solutions cover all aspects of cloud server maintenance, including load balancing, patch management, data backups, and disaster recovery planning. Our experienced professionals work with cutting-edge tools to ensure that your servers are secure, efficient, and scalable to meet changing business needs. Whether you operate in e-commerce, finance, or technology, we tailor our services to align with your operational goals. With Atcuality as your trusted partner, you can focus on driving growth while we handle the technical complexities of cloud management.
#seo marketing#seo services#artificial intelligence#azure cloud services#seo agency#digital marketing#seo company#iot applications#ai powered application#amazon web services#ai applications#virtual reality#augmented reality agency#augmented human c4 621#augmented and virtual reality market#augmented intelligence#augmented reality#cloud security services#cloud computing#cloud services#cloud service provider#cloud server hosting#software#devops#information technology#cash collection application#task management#blockchain#web developing company#web development
2 notes
·
View notes
Text
Choosing the right cloud disaster recovery solution requires careful consideration of factors like Recovery Point Objectives (RPO), Recovery Time Objectives (RTO), data security, scalability, cost, and vendor reliability. Implementing best practices can minimize downtime and data loss, ensuring that businesses remain resilient during disasters.
#cloud disaster recovery#cloud DR solution#business continuity#disaster recovery plan#RPO#RTO#data security#scalable recovery#cloud DR vendors#disaster recovery testing#geographic redundancy
0 notes
Text
(2024-05-01) Presenting A Session At "European Identity and Cloud Conference 2024"
On Friday, June 7th, I will be presenting a session at “European Identity and Cloud Conference 2024”. Very honored to be selected as a speaker and to contribute to helping others. For more information about the conference, please see: https://www.kuppingercole.com/events/eic2024 For more information about my session, please see: https://www.kuppingercole.com/sessions/5699/1 On Thursday, June…

View On WordPress
#Active Directory#cybersecurity#Disaster Recovery#Entra Cloud Sync#Entra Connect Sync#Ransomware#Security
0 notes
Text
The Importance of a Disaster Recovery Solution by Zimcom

In today's fast-paced and digitally driven business landscape, data is the lifeblood of organizations. From financial records to customer information and critical applications, the reliance on data is paramount. However, with great reliance comes great responsibility – the responsibility to protect this invaluable asset, especially in the face of unforeseen disasters. This is where a robust disaster recovery solution, such as the one offered by Zimcom, becomes not just a luxury but a necessity.
Understanding Disaster Recovery:
Disasters can take many forms, from natural calamities like hurricanes and earthquakes to human-made disasters such as cyberattacks or hardware failures. Regardless of their origin, these disasters have the potential to disrupt business operations and lead to data loss.
The Role of Disaster Recovery:
A disaster recovery (DR) solution is a meticulously planned and executed strategy that ensures an organization can continue its essential functions during and after a disaster. It is not just about backing up data; it's about creating a comprehensive plan that includes:
Data Backup: Regular and secure backups of critical data to ensure minimal data loss in the event of a disaster.
Redundancy: Duplicate systems and infrastructure that can seamlessly take over if the primary systems fail.
Failover Mechanisms: Automated processes that shift operations to backup systems without manual intervention.
Testing: Rigorous testing and simulations to ensure that the DR plan works as expected.
Why Zimcom's Disaster Recovery Solution Stands Out:
Zimcom has been at the forefront of disaster recovery solutions for years, and their expertise in this area is unmatched. Here's why their solution is a cut above the rest:
Tailored Solutions: Zimcom understands that one size doesn't fit all. They work closely with each client to create a disaster recovery plan that aligns with their unique needs and business processes.
Cutting-Edge Technology: Zimcom constantly invests in the latest technologies to ensure that their disaster recovery solutions are not just effective but also efficient.
24/7 Support: Disasters can strike at any time. Zimcom offers round-the-clock support to ensure that their clients have assistance when they need it the most.
Data Security: Security is paramount when dealing with sensitive data. Zimcom's disaster recovery solutions include robust encryption and data protection measures.
Compliance and Regulations: Zimcom keeps up to date with industry regulations and ensures that their solutions comply with legal requirements, offering peace of mind to their clients.
The Real Cost of Not Having Disaster Recovery:
The consequences of not having a reliable disaster recovery solution in place can be catastrophic. Data loss can lead to financial losses, damage to a company's reputation, and even legal repercussions in some cases. Furthermore, downtime during recovery can have a crippling effect on productivity.
Conclusion:
In today's digital age, where data is more valuable than ever, a disaster recovery solution is not just an option; it's a strategic necessity. Zimcom's disaster recovery solution offers businesses the peace of mind that their data is safe and that they can continue their operations even in the face of adversity. Don't wait until disaster strikes – invest in a robust disaster recovery plan today, and safeguard your organization's future.
#Internet solutions#Secure Cloud Hosting#Cloud migration services#Disaster recovery solution#Cloud network security#Managed cloud services#Cloud Migration#Data Center Services
1 note
·
View note
Text
Protect Your Business with Disaster Recovery Backup and IT Managed Services in Woodland Hills
Protect your business from unexpected disruptions with Disaster Recovery Backup and IT Managed Services in Woodland Hills. In today’s technology-driven world, data loss or system failures can have a serious impact on your operations. Having a reliable disaster recovery plan in place is essential to safeguard your business and ensure continuity when facing challenges like cyberattacks, natural disasters, or hardware malfunctions.
Disaster Recovery Backup solutions provide businesses with a safety net by regularly backing up critical data and ensuring that it can be restored quickly when needed. These services are designed to minimize downtime and prevent permanent data loss, allowing your business to recover smoothly and continue operations even after a major disruption. With cloud-based and off-site backups, you’ll have peace of mind knowing your data is secure and always accessible.
IT Managed Services in Woodland Hills offer comprehensive support to keep your business running efficiently. From monitoring your network and managing cybersecurity to handling software updates and troubleshooting, managed IT services ensure that your technology infrastructure is always optimized and secure. By outsourcing your IT needs, you can focus on your core business activities while experts handle your IT maintenance and security, ensuring you’re protected against potential threats.
Combining Disaster Recovery Backup and IT Managed Services provides your business with a complete protection plan, safeguarding both your data and your systems. This proactive approach reduces the risk of costly downtime, strengthens your cybersecurity defenses, and ensures fast recovery in the event of a disaster.
For businesses in Woodland Hills, investing in these solutions is a critical step toward long-term success. Protect your data, secure your systems, and ensure business continuity with professional Disaster Recovery Backup and IT Managed Services today.
#GoodSuite#DisasterRecoveryBackup#ManagedITServices#WoodlandHillsBusiness#ITSupport#BusinessContinuity#DataProtection#ITSolutions
2 notes
·
View notes
Text
CrowdStrike Outage: Customers Independent Cybersecurity Firm

Supporting customers during the CrowdStrike outage Independent cybersecurity firm. CrowdStrike launched a software upgrade that started affecting IT systems all across the world. They would like to provide an update on the efforts that were made with CrowdStrike and others to remedy and help consumers, even though this was not a Microsoft issue and it affects the entire ecosystem.
CrowdStrike outage
Everyone have been in constant contact with customers, CrowdStrike outage, and outside developers since the start of this incident in order to gather data and hasten resolutions. It are aware of the impact this issue has brought to many people’s everyday routines as well as companies. The primary objective is to help customers safely restore interrupted systems back online by offering technical advice and support. Among the actions made are:
Using CrowdStrike to automate their solution development process.
In addition to providing a workaround recommendation, CrowdStrike has made a public statement on this vulnerability.
The Windows Message Centre contained instructions on how to fix the issue on Windows endpoints.
Deploying hundreds of engineers and specialists from Microsoft to collaborate directly with clients in order to restore services.
In order to inform ongoing discussions with CrowdStrike and customers, us are working together with other cloud providers and stakeholders, such as Google Cloud Platform (GCP) and Amazon Web Services (AWS), to share awareness on the state of effect they are each witnessing throughout the sector.
publishing the scripts and documentation for manual cleanup as soon as possible.
Customers will be updated on the incident’s status via the Azure Status Dashboard, available here.
They are constantly updating and supporting customers while working around the clock.
CrowdStrike has also assisted us in creating a scalable solution that would speed up Microsoft’s Azure infrastructure’s correction of CrowdStrike’s flawed update.
They have also collaborated on the most efficient methods with AWS and GCP.
CrowdStrike update
Software changes might occasionally create disruptions, but major events like the CrowdStrike event don’t happen often. As of right now, researchers calculate that 8.5 million Windows devices less than 1% of all Windows computers were impacted by CrowdStrike’s update. Even though the percentage was low, the usage of CrowdStrike by businesses that manage numerous vital services has a significant influence on the economy and society.
This event highlights how intertwined the large ecosystem consisting of consumers, software platforms, security and other software vendors, and worldwide cloud providers is. It serves as a reminder of how critical it is that everyone in the tech ecosystem prioritizes disaster recovery utilising existing channels and safe deployment practices.
As the past two days have demonstrated, cooperation and teamwork are the keys to learning, healing, and forward motion. They value the cooperation and teamwork of everyone in this sector, and will continue to keep you informed about the results and future plans.
Overview
An CrowdStrike outage can be a difficult occurrence for any organisation in the ever-changing field cybersecurity . Their resilience and readiness were put to the test recently when a significant CrowdStrike outage affected customers. This post seeks to give a thorough explanation of how they supported the clients at this crucial time, making sure their cybersecurity requirements were satisfied with the highest effectiveness and consideration.
Comprehending the CrowdStrike Incident
One of the top cybersecurity companies’ services experienced problems due to the unanticipated CrowdStrike outage. Many organizations were affected by the outage, which made them susceptible to possible cyberattacks. The primary objective was to minimize the effects of this outage on customers while maintaining security services for them.
Quick Reaction to the Outage
Upon detecting the outage, the dedicated employees moved quickly to resolve it. They prioritized communicating with clients due to recognized the seriousness of the matter. Below is a thorough explanation of the prompt response:
Notification and Communication: Everyone immediately sent out a notification of the outage by email, phone calls, and through own support portal to all impacted clients. Having open and honest communication was essential to reassuring and informing those who hired us.
Activation of the Incident Response Team: They promptly activated the incident response team, which is made up of support engineers and cybersecurity specialists. To evaluate the effects of the outage and create a tactical reaction strategy, this team worked nonstop.
Providing Differential Approaches to Security
Ensuring customers have strong security was the initial focus during the downtime. To guarantee ongoing protection, having put in place a number of other security measures, including:
Temporary Security Solutions: In order to cover for the CrowdStrike outage, they implemented temporary security solutions. Advanced threat intelligence tools, more intrusion detection systems, and improved firewall setups were some of these answers.
Alerts and Manual Monitoring: They increased the manual monitoring efforts at its Security Operations Centre (SOC). In order to ensure prompt action in the event of an incident, having installed extra alarm mechanisms to identify any unusual activity that would point to possible cyber attacks.
Improving Customer Service
It strengthened the support infrastructure in order to reply to the worries and questions of the clients:
24/7 Support Availability: They have extended support service hours to offer assistance whenever you need it. Clients could get in touch with the support team whenever they needed assistance, so they could get it quickly.
Specialised Support Channels: Everyone set up special support channels for problems relating to outages. This made it possible for us to concentrate on helping the impacted clients and to expedite the support process.
Constant Observation and Updates
They continued to provide updates throughout the interruption due to the were committed to being open and satisfying those who trust us:
Regular Status Updates: Having kept you informed on the status of the issue resolution process on a regular basis. The actions being taken to resume regular services and the anticipated time frames for resolution were noted in these updates.
Integration of Customer comments: In order to better understand the client’s unique wants and concerns, and actively sought out their comments. This input was really helpful to us because it adjusted the way to replied and enhanced the assistance offerings.
Acquiring Knowledge and Developing from Experience
They carried out a comprehensive investigation following the CrowdStrike outage in order to pinpoint problem areas and guarantee enhanced readiness for upcoming incidents:
Root Cause Analysis: To identify the causes of the CrowdStrike outage, their team conducted a thorough root cause analysis. They were able to pinpoint areas that required improvement and weaknesses thanks to their investigation.
Process Improvements: Having carried out a number of process enhancements in light of the new information. These included modernizing the security architecture, strengthening communication tactics, and refining the incident response procedures.
Enhancing Their Collaboration with CrowdStrike
Nous collaborated closely with CrowdStrike outage to quickly resolve the issue due to recognized their crucial position in the cybersecurity ecosystem:
Cooperation and Support: In order to guarantee a prompt resolution, they worked in tandem with CrowdStrike’s engineering and technical support teams. They were able to efficiently utilize CrowdStrike’s resources and experience thanks to working together with them.
Post-Outage Review: To assess the CrowdStrike outage and its effects, they jointly reviewed with CrowdStrike once services had fully recovered. This review was crucial to strengthening cooperation and improving the capacity to respond as a team.
In summary
Although the CrowdStrike outage was a difficult occurrence, all proactive and customer-focused strategy made sure that customers got the assistance and security they required. It lies in the unwavering commitment to enhancing its infrastructure and services to deliver the best possible cybersecurity. The desire to remain a dependable and trustworthy partner for their clients, protecting their digital assets from any danger, has been reinforced by what happened during this CrowdStrike outage
Read more on govindhtech.com
#crowdstrikeoutage#CrowdStrike#cybersecurity#Microsoft#MicrosoftAzure#securityoperationscentre#AWS#news#technews#technology#technologynews#technologytrends#govindhtech
2 notes
·
View notes